Ниллион (NIL) — Сеть шифрования слепых вычислений
Что такое Ниллион?
Nillion - это децентрализованная сеть вычислений для обеспечения конфиденциальности, разработанная для решения основных проблем конфиденциальности данных с использованием технологии "Слепых вычислений". Подобно тому, как блокчейн обеспечивает децентрализованное доверие для транзакций, Nillion создает безопасную среду для хранения и обработки ценных данных без необходимости доверенных посредников. Его основное новшество позволяет обрабатывать данные, оставаясь зашифрованными на протяжении всего процесса, устраняя традиционные шаги "дешифровать-вычислить-зашифровать" и тем самым снижая риск утечки данных.
Для обеспечения здоровья и стабильности сети Nillion позволяет валидаторам зарабатывать награды за свой вклад. На 10 марта более 500 000 валидаторов обработали примерно 196 миллионов шифротекстов, обеспечивая около 1066 ГБ данных. Кроме того, Nillion интегрировалась с блокчейнами, такими как Near, Aptos и Arbitrum, и сформировала глубокие партнерства с десятками проектов в различных областях, включая инфраструктуру, искусственный интеллект, социальные медиа и DeFi.
Gate.com теперь поддерживает торговлю на месте $NIL
Зачем нужен Nillion?
В контексте взрывного роста цифровой экономики глобальные потери от утечек данных ежегодно составляют примерно 4,35 триллиона долларов. Традиционные системы защиты конфиденциальности сталкиваются с тремя основными проблемами: во-первых, кризис централизованного доверия, когда предприятия/учреждения контролируют данные пользователей, что приводит к единичным точкам отказа; во-вторых, парадокс безопасности и эффективности, когда улучшенное шифрование часто приводит к резкому снижению вычислительной эффективности; и, в-третьих, дилемма конфиденциальности в эпоху искусственного интеллекта, где обучение больших моделей требует огромных объемов данных, но чувствительные данные в областях здравоохранения и финансов сложно распространять из-за рисков соответствия.
Архитектура слепых вычислений Nillion позволяет владельцам данных полностью контролировать процесс, даже во время многопользовательских совместных вычислений, где каждый участник может получить доступ только к результатам вычислений без возможности отследить исходные данные. Например, медицинские учреждения могут совместно обучать модели диагностики искусственного интеллекта, сохраняя данные пациентов в зашифрованном виде. Эта функция "полезно, но невидимо" может увеличить эффективность освобождения стоимости данных на 300%, снижая риски утечки до уровня, который даже квантовые компьютеры не смогут взломать. В плане соблюдения нормативных требований технология доказательства хранения с нулевым разглашением Nillion может предоставить соответствующие следы аудита, соответствуя требованиям таких регламентов, как GDPR (Общий регламент по защите данных).
Архитектура сети Nillion
Архитектура сети Nillion состоит из двух основных компонентов: Petnet и nilChain. Petnet позволяет строителям использовать технологии, улучшающие конфиденциальность (PET), для хранения и вычисления данных, сохраняя их в зашифрованном виде. nilChain поддерживает платежи и стимулирует участие в сети Nillion.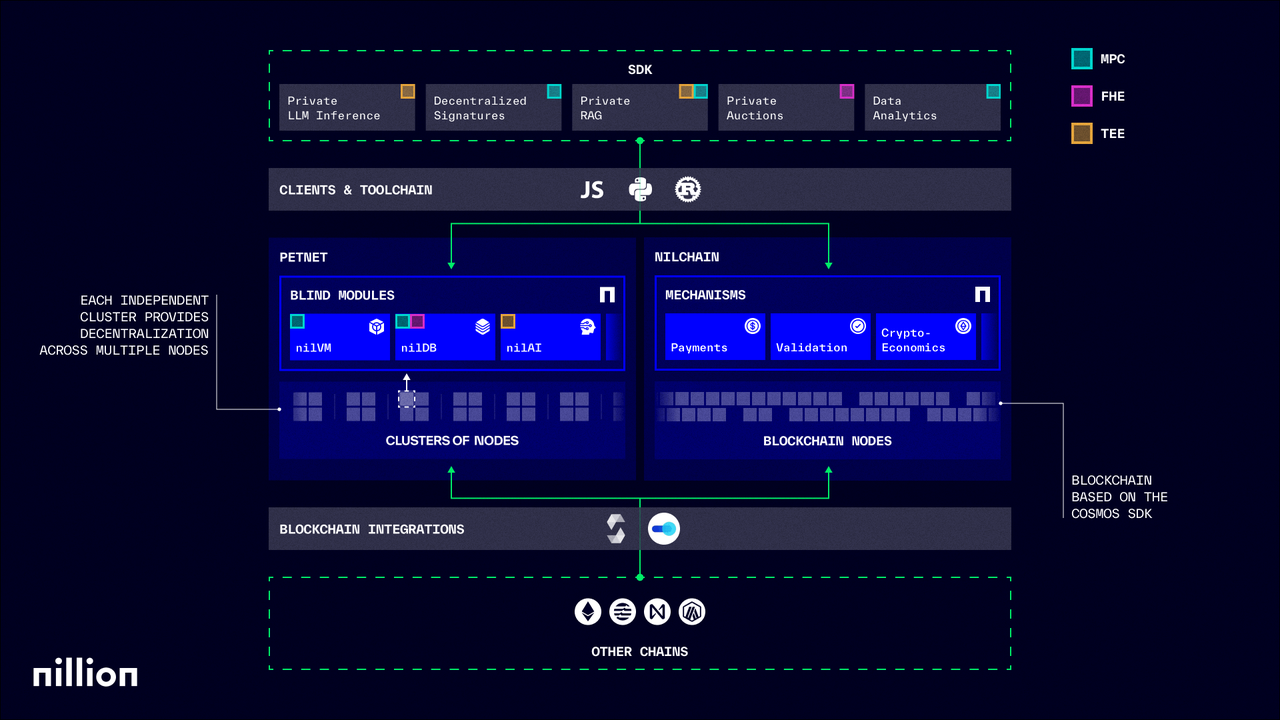
Petnet
Petnet - это оркестровый уровень сети Nillion, состоящий из сети узлов. Узлы поддерживают безопасное хранение и обработку данных, которые можно использовать с помощью различных SDK, доступных для взаимодействия с узлами. Каждый узел может выбрать один или несколько слепых модулей для хранения и обработки данных. Каждый слепой модуль оснащен одним или несколькими технологиями, улучшающими конфиденциальность (PET), включая безопасные многосторонние вычисления (MPC), гомоморфное шифрование (HE) и доверенные исполнительные среды (TEE), позволяя разработчикам выбирать в зависимости от реальных потребностей приложения.
nilChain
nilChain - это координационный уровень сети Nillion, управляющий общими ресурсами всей сети Nillion. Он не участвует непосредственно в слепых вычислениях, но отвечает за межкластерную координацию и поддерживает платежи, стейкинг валидаторов, вознаграждения и управление. Уровень координации построен с использованием Cosmos SDK и поддерживает IBC для совместимости.
Рабочий процесс
Отправка данных: Пользователи шифруют и делят данные между узлами Petnet.
Вычислительный запрос: Смарт-контракты определяют слепые вычислительные задачи.
Распределение задач: Petnet соотносит узлы для обработки зашифрованных данных совместно.
Результат доставки: Зашифрованные результаты возвращаются; только держатели ключей могут расшифровать.
Расчет поощрений: nilChain распределяет награды NIL на основе вкладов узлов.
Пример: страховые выплаты
Пользователь хранит зашифрованные медицинские данные в SecretVault (модуль nilDB).
Страховщик отправляет запрос на смарт-контракт.
Узлы Petnet проверяют критерии требований с использованием слепого вычисления.
Доказательства нулевого знания результатов отправляются в nilChain.
Выплаты USDC запускаются автоматически без расшифровки сырых данных.
Технология слепых модулей
nilDB
nilDB - это распределенная зашифрованная база данных, использующая алгоритм разделения секрета Шамира для разделения и хранения данных. Утечка одного узла приводит только к непонятным фрагментам, и ни один узел не содержит полного набора данных. В отличие от обычных баз данных NoSQL, nilDB устраняет зависимость от центрального органа путем распределения зашифрованных данных в виде секретных акций по нескольким узлам.
nilAI
nilAI - это фреймворк искусственного интеллекта, сохраняющий конфиденциальность, интегрированный с ускорением NVIDIA CUDA, поддерживающий выполнение больших языковых моделей в средах TEE. nilAI включает три технологии: AIVM, nada-AI и nilTEE. AIVM гарантирует, что узлы поддерживают слепоту по отношению к запросам пользователя и выводам модели, nada-AI обеспечивает легкую среду разработки искусственного интеллекта, а nilTEE отвечает за выполнение среды TEE. nilAI использует шифрование градиента передачи, обеспечивая, что даже во время обучения модели участники не могут обратно разработать исходные данные.
nilVM
nilVM - это безопасная виртуальная машина, настроенная на основе набора инструкций RISC-V, спроектированная с архитектурой шифрования памяти шины и написанная на Nada, специализированном языке области деятельности (DSL) Nillion на основе Python. Каждая область памяти в nilVM использует независимые ключи, что делает невозможным расшифровку даже в случае извлечения данных памяти при физических атаках. В сочетании с инструментами формальной верификации nilVM может доказать, что процесс выполнения кода не имеет утечек через боковые каналы.
Финансирование фона
- Декабрь 2022 года: Nillion объявил о завершении раунда финансирования на сумму $20 млн под руководством Distributed Global с участием GSR, OP Crypto и SALT Fund.
- Октябрь 2024 года: Nillion объявила о завершении раунда финансирования на сумму 25 миллионов долларов, возглавляемого Hack VC, с участием Distributed Global.
Nillion Токеномика
Токен Утилита
NIL - это внутренний утилитарный токен Nillion:
- Сервисы координации: NIL используется для транзакций в слое координации, доступа к сетевым ресурсам и урегулирования затрат на использование по всей сети. Как механизм передачи стоимости сети, NIL обеспечивает беспрепятственное взаимодействие между компонентами системы.
- Доступ к вычислениям в слепом режиме: разработчики и пользователи могут использовать NIL для доступа к передовым функциям хранения данных и вычислений, обеспечивая услуги для своих приложений. Будь то использование SecretVault для хранения конфиденциальных данных или запуск частных моделей искусственного интеллекта через SecretLLM, NIL является ключом к разблокировке этих услуг.
- Механизм стейкинга: Владельцы токенов могут ставить NIL для поддержки безопасности сети и заработка наград. Валидаторы обеспечивают безопасность сети, привязывая свои токены для проверки транзакций и вычислений, обеспечивая пассивный доход для владельцев токенов и повышая общую безопасность и устойчивость сети.
- Функционал управления: держатели токенов NIL имеют право участвовать в децентрализованном управлении, предлагая и голосуя за ключевые сетевые решения, включая обновления протокола и настройки параметров.
Распределение токенов
Общий объем токенов NIL составляет 1 миллиард, с начальным циркулирующим предложением в 195,15 миллиона (19,52% от общего предложения).
- 29% для экосистемы и развития
- 20% для сообщества
- 10% на развитие протокола
- 21% для ранних сторонников
- 20% для основных участников

Похожие статьи

Кто такой Сатоши Накамото?

Отчет об исследовании Uniswap (UNI)

Отчет о исследовании Immutable X (IMX)

Отчет об исследовании Kaspa (KAS)

Отчет об исследовании Pendle (PENDLE)


